TryHackMe Walkthrough - 25 Days of Cyber Security (Day 16-20)
Complete solutions and explanations for days 16–20 of the 25 Days of Cyber Security challenge on TryHackMe

You can find days 11-15 here.
Table of Contents:
Day 16
Oh no! Santa 🎅 has taken off, leaving you -- the faithful elves behind! Can you help find Santa's location?
Luckily, the elves are OSINT masters and remember a thing or two. Specifically, they remember:
Santa has a webpage at MACHINE_IP/static/index.html to help lost elves find their way home. Santa never told the elves what port number the webserver is on. Can you find out?!
This webpage has a link somewhere on it, hidden away so anyone that isn't an elf can't find it.
Santa's Sled has an API we can talk too. The key for the API is between 0 and 100, and it's an odd number. But be careful! After an unknown number of attempts, Santa's Sled will ban your IP address.
Questions:
What is the port number for the web server?
Just run a quick nmap scan or guess the port. Its pretty common
root@ip-10-82-110-227:~# nmap 10.82.187.184
Starting Nmap 7.80 ( https://nmap.org ) at 2026-01-25 19:54 GMT
mass_dns: warning: Unable to open /etc/resolv.conf. Try using --system-dns or specify valid servers with --dns-servers
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 10.82.187.184
Host is up (0.00012s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.33 seconds
Click to reveal
80
Without using enumerations tools such as Dirbuster, what is the directory for the API? (without the API key)
I guessed the pretty obvious directory
Click to reveal
api
Where is Santa right now?
We can write a script that brute forces every odd number. Somethink like this:
import requests
base_url = "http://10.82.187.184/api/"
for number in range(1, 100, 2): # odd numbers only
url = f"{base_url}{number}"
try:
response = requests.get(url, timeout=5)
print(f"Trying {number}: {response.status_code} -> {response.text}")
except requests.exceptions.RequestException as e:
print(f"Error with {number}: {e}")
Output:
root@ip-10-82-110-227:~# python3 bruteforce.py
Trying 1: 200 -> {"item_id":1,"q":"Error. Key not valid!"}
Trying 3: 200 -> {"item_id":3,"q":"Error. Key not valid!"}
Trying 5: 200 -> {"item_id":5,"q":"Error. Key not valid!"}
Trying 7: 200 -> {"item_id":7,"q":"Error. Key not valid!"}
Trying 9: 200 -> {"item_id":9,"q":"Error. Key not valid!"}
Trying 11: 200 -> {"item_id":11,"q":"Error. Key not valid!"}
Trying 13: 200 -> {"item_id":13,"q":"Error. Key not valid!"}
Trying 15: 200 -> {"item_id":15,"q":"Error. Key not valid!"}
Trying 17: 200 -> {"item_id":17,"q":"Error. Key not valid!"}
Trying 19: 200 -> {"item_id":19,"q":"Error. Key not valid!"}
Trying 21: 200 -> {"item_id":21,"q":"Error. Key not valid!"}
Trying 23: 200 -> {"item_id":23,"q":"Error. Key not valid!"}
Trying 25: 200 -> {"item_id":25,"q":"Error. Key not valid!"}
Trying 27: 200 -> {"item_id":27,"q":"Error. Key not valid!"}
Trying 29: 200 -> {"item_id":29,"q":"Error. Key not valid!"}
Trying 31: 200 -> {"item_id":31,"q":"Error. Key not valid!"}
Trying 33: 200 -> {"item_id":33,"q":"Error. Key not valid!"}
Trying 35: 200 -> {"item_id":35,"q":"Error. Key not valid!"}
Trying 37: 200 -> {"item_id":37,"q":"Error. Key not valid!"}
Trying 39: 200 -> {"item_id":39,"q":"Error. Key not valid!"}
Trying 41: 200 -> {"item_id":41,"q":"Error. Key not valid!"}
Trying 43: 200 -> {"item_id":43,"q":"Error. Key not valid!"}
Trying 45: 200 -> {"item_id":45,"q":"Error. Key not valid!"}
Trying 47: 200 -> {"item_id":47,"q":"Error. Key not valid!"}
Trying 49: 200 -> {"item_id":49,"q":"Error. Key not valid!"}
Trying 51: 200 -> {"item_id":51,"q":"Error. Key not valid!"}
Trying 53: 200 -> {"item_id":53,"q":"Error. Key not valid!"}
Trying 55: 200 -> {"item_id":55,"q":"Error. Key not valid!"}
Trying 57: 200 -> {"item_id":57,"q":"Winter Wonderland, Hyde Park, London."}
Trying 59: 200 -> {"item_id":59,"q":"Error. Key not valid!"}
Click to reveal
Vertical
Find out the correct API key. Remember, this is an odd number between 0-100. After too many attempts, Santa's Sled will block you.
Click to reveal
Vertical
Day 17
McSkidy has never really touched low-level languages - this is something they must learn in their quest to defeat the Christmas monster.
Questions:
What is the value of local_ch when its corresponding movl instruction is called (first if multiple)?
Open the challenge file with radare2: r2 -d ./challenge1
Now we can look at the main function and we get the answer for the first question:
[0x00400a30]> pdf @main
;-- main:
/ (fcn) sym.main 35
| sym.main ();
| ; var int local_ch @ rbp-0xc
| ; var int local_8h @ rbp-0x8
| ; var int local_4h @ rbp-0x4
| ; DATA XREF from 0x00400a4d (entry0)
| 0x00400b4d 55 push rbp
| 0x00400b4e 4889e5 mov rbp, rsp
| 0x00400b51 c745f4010000. mov dword [local_ch], 1
| 0x00400b58 c745f8060000. mov dword [local_8h], 6
| 0x00400b5f 8b45f4 mov eax, dword [local_ch]
| 0x00400b62 0faf45f8 imul eax, dword [local_8h]
| 0x00400b66 8945fc mov dword [local_4h], eax
| 0x00400b69 b800000000 mov eax, 0
| 0x00400b6e 5d pop rbp
\ 0x00400b6f c3 ret
Click to reveal
1
What is the value of eax when the imull instruction is called?
Okay, lets go trough the instructions:
0x00400b51 c745f4010000. mov dword [local_ch], 1
- local_ch is set to 1
0x00400b58 c745f8060000. mov dword [local_8h], 6
- local_8h is set to 6
0x00400b5f 8b45f4 mov eax, dword [local_ch]
- the value of local_ch is loaded into eax, so eax = 1
0x00400b62 0faf45f8 imul eax, dword [local_8h]
- eax is multiplied with local_8h, so 1*6=6
Click to reveal
6
What is the value of local_4h before eax is set to 0?
Keep following the instructions:
0x00400b66 8945fc mov dword [local_4h], eax
- we know eax now is 6. so local_4h is assigned the value 6
0x00400b69 b800000000 mov eax, 0
Click to reveal
6
Day 18
"Silly Santa...Forgetting his password yet again!" complains Elf McEager. However, it is in fact Elf McEager who is silly for not creating a way to reset Santa's password for the TBFC dashboard.Santa needs to get back into the dashboard for Christmas! Can you help Elf McEager reverse engineer TBFC's application to retrieve the password for Santa?!
Questions:
Open the "TBFC_APP" application in ILspy and begin decompiling the code
-No answer needed
What is Santa's password?
You have to took at the MainForm in the Method private unsafe void buttonActivate_Click(object sender, EventArgs e)
You will find the hardcoded passowrd:
private unsafe void buttonActivate_Click(object sender, EventArgs e)
{
IntPtr value = Marshal.StringToHGlobalAnsi(textBoxKey.Text);
sbyte* ptr = (sbyte*)System.Runtime.CompilerServices.Unsafe.AsPointer(ref <Module>.??_C@_0BB@IKKDFEPG@santapassword321@);
void* ptr2 = (void*)value;
byte b = *(byte*)ptr2;
byte b2 = 115;
if ((uint)b >= 115u)
{
while ((uint)b <= (uint)b2)
{
if (b != 0)
{
ptr2 = (byte*)ptr2 + 1;
ptr++;
b = *(byte*)ptr2;
b2 = (byte)(*ptr);
if ((uint)b < (uint)b2)
{
break;
}
continue;
}
MessageBox.Show("Welcome, Santa, here's your flag thm{046af}", "That's the right key!", MessageBoxButtons.OK, MessageBoxIcon.Asterisk);
return;
}
}
MessageBox.Show("Uh Oh! That's the wrong key", "You're not Santa!", MessageBoxButtons.OK, MessageBoxIcon.Hand);
}Click to reveal
santapassword321
Now that you've retrieved this password, try to login...What is the flag?
I found this in ILSpy while looking for the password:
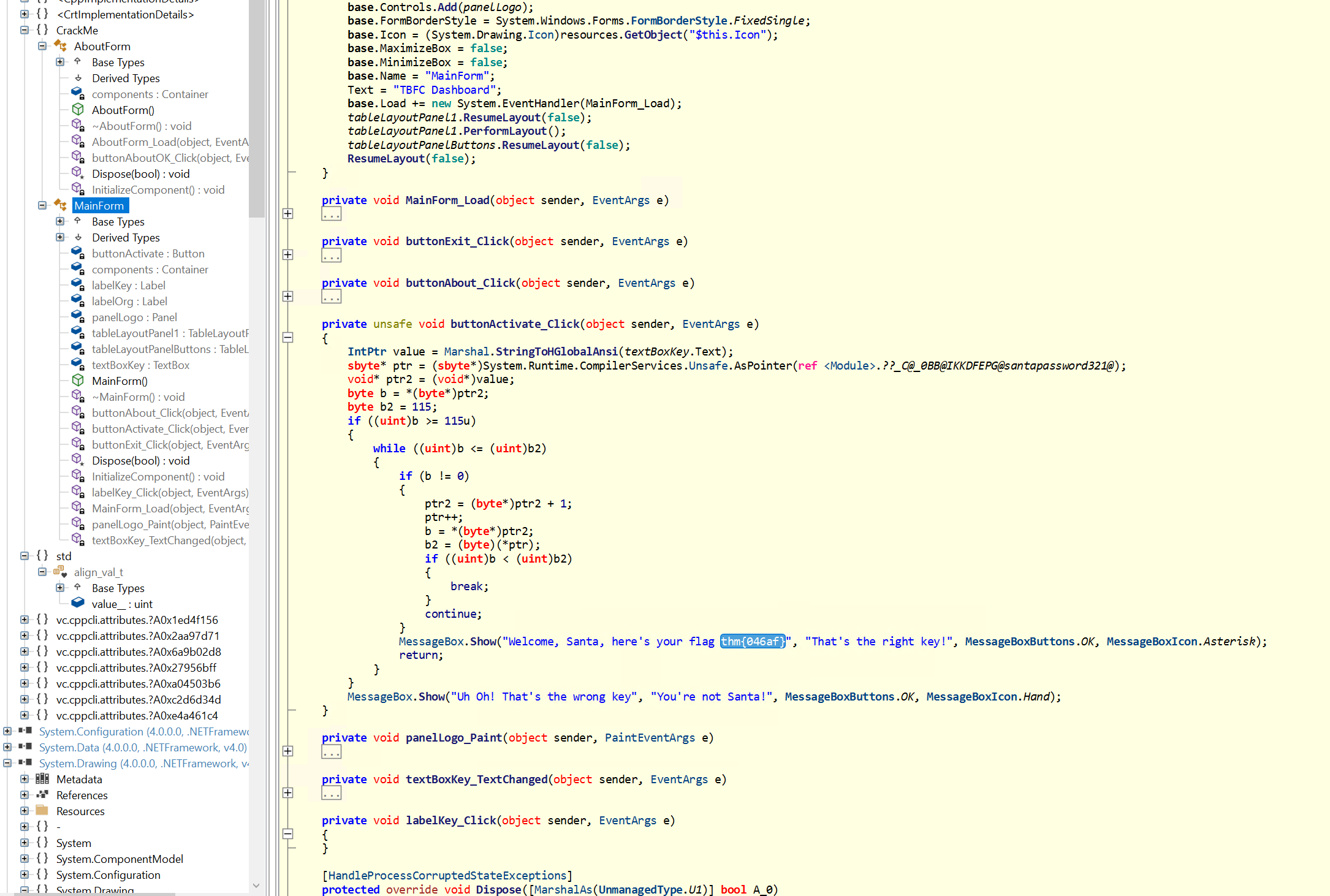
Click to reveal
thm{046af}
Day 19
Santa has released a web app that lets the children of the world check whether they are currently on the naughty or nice list. Unfortunately, the elf who coded it exposed more things than she thought. Can you access the list administration and ensure that every child gets a present from Santa this year?
Feel free to try hacking this web app on your own, or follow the instructions below! Note: when bypassing the hostname filter, use localtest.me otherwise your attempts won't work!
Can't bypass the naughty or nice list yourself? Watch the creator (@Tib3rius) solve today's challenge.!
Questions:
What is Santa's password?
You get the password while following the Guide.
Visit http://10.82.185.232/?proxy=http%3A%2F%2Flist.hohoho.localtest.me and you will see it.
You have to guess the username. It's Santa
Click to reveal
Be good for goodness sake!
What is the challenge flag?
Click to reveal
THM{EVERYONE_GETS_PRESENTS}
Day 20
Someone is mischievous at The Best Festival Company. The contents within the stockings have been removed. A clue was left in one of the stockings that hints that the contents have been hidden within Elfstation1. McEager moves quickly and attempts to RDP into the machine. Yikes! He is unable to log in.
Luckily, he has been learning PowerShell, and he can remote into the workstation using PowerShell over SSH.
Task: Use the PowerShell console to navigate throughout the endpoint to find the hidden contents to reveal what was hidden in the stockings.
Questions:
Search for the first hidden elf file within the Documents folder. Read the contents of this file. What does Elf 1 want?
The first one is easy. Change into the Documents folder. Now look for all files (including hidden)
PS C:\Users\mceager> cd Documents
PS C:\Users\mceager\Documents> Get-ChildItem -File -Hidden
Directory: C:\Users\mceager\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 12/7/2020 10:29 AM 402 desktop.ini
-arh-- 11/18/2020 5:05 PM 35 e1fone.txt
PS C:\Users\mceager\Documents> Get-Content e1fone.txt
All I want is my '2 front teeth'!!! Click to reveal
2 front teeth
Search on the desktop for a hidden folder that contains the file for Elf 2. Read the contents of this file. What is the name of that movie that Elf 2 wants?
We basically have to do the same think, but now we have to look for a hidden folder
PS C:\Users\mceager\Desktop> Get-ChildItem -Directory -Hidden
Directory: C:\Users\mceager\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--h-- 12/7/2020 11:26 AM elf2wo
PS C:\Users\mceager\Desktop> cd elf2wo
PS C:\Users\mceager\Desktop\elf2wo> ls
Directory: C:\Users\mceager\Desktop\elf2wo
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/17/2020 10:26 AM 64 e70smsW10Y4k.txt
PS C:\Users\mceager\Desktop\elf2wo> Get-Content e70smsW10Y4k.txt
I want the movie Scrooged <3!
Click to reveal
Scrooged
Search the Windows directory for a hidden folder that contains files for Elf 3. What is the name of the hidden folder? (This command will take a while)
Change into the Windows directory and search recursively with the filter *3*
PS C:\Windows> Get-Childitem -Recurse -Directory -Hidden -ErrorAction SilentlyContinue -Filter "*3*"
Directory: C:\Windows\System32
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--h-- 11/23/2020 3:26 PM 3lfthr3e
Click to reveal
3lfthr3e
How many words does the first file contain?
Get the content of the file and pipe it into Measure-Object -Word
PS C:\Windows\System32\3lfthr3e> Get-Childitem -File -Hidden
Directory: C:\Windows\System32\3lfthr3e
Mode LastWriteTime Length Name
---- ------------- ------ ----
-arh-- 11/17/2020 10:58 AM 85887 1.txt
-arh-- 11/23/2020 3:26 PM 12061168 2.txt
PS C:\Windows\System32\3lfthr3e> get-Content 1.txt | Measure-Object -Word
Lines Words Characters Property
----- ----- ---------- --------
9999
Click to reveal
9999
What 2 words are at index 551 and 6991 in the first file?
Get the content using the index
PS C:\Windows\System32\3lfthr3e> (Get-Content -Path 1.txt)[551]
Red
PS C:\Windows\System32\3lfthr3e> (Get-Content -Path 1.txt)[6991]
Ryder
Click to reveal
Red Ryder
This is only half the answer. Search in the 2nd file for the phrase from the previous question to get the full answer. What does Elf 3 want? (use spaces when submitting the answer)
Use the Select-String command and search for the Pattern Ryder
PS C:\Windows\System32\3lfthr3e> Select-String 2.txt -Pattern "Ryder"
2.txt:558704:redryderbbgun
Click to reveal
Red Ryder BB Gun
You can find days 11-15 here TryHackMe Walkthrough - 25 Days of Cyber Security (Day 11-15)
You can find more of my posts and projects here: https://blog.janalhorn.de



